How Hackers Kick Victims Off of Wireless Networks
How Hackers Kick Victims Off of Wireless Networks
Hello, my fellow hackers! Today we’re going to be covering a little bit of Wi-Fi hacking. Specifically, we’re going to be learning how to kick other people off of wireless networks, even when we’re not connected to it ourselves! We’re going to be using an external wireless adapter for this, so if you don’t have one, I highly recommend getting one, as it is an essential piece of equipment for hacking Wi-Fi! The wireless adapter I’ll be using for this lesson is the Atheros Ar9271, which is capable of packet injection (injection is a very important feature to have for our wireless adapter). Now that we’ve got all that out of the way, let’s get started!
Step 1: Configure the Wireless Adapter for the Attack
If we’re going to use our wireless adapter for this attack, we’ll need to configure it to do so! First, let’s take an overview look at our current wireless adapter setup:
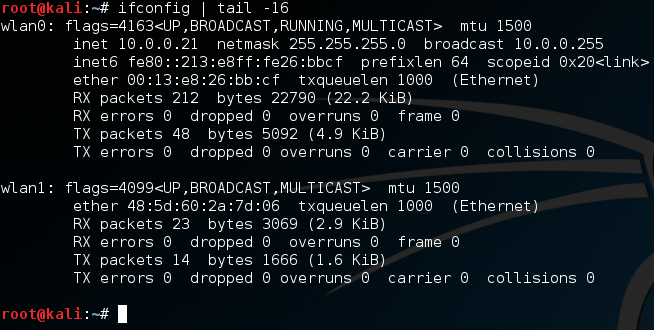
Now, for this demonstration attack, we’re going to connect our built-in wireless card (wlan0) to the target network. Then, we’ll use our external wireless adapter (wlan1) to kick ourselves off the network. Next, let’s put our external adapter into monitor mode:
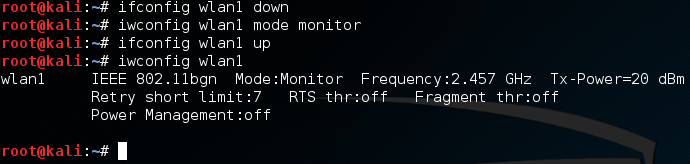
First, we use ifconfig to set the interface down. Then, we use iwconfig to change it to monitor mode, then we’ll bring it right back up. Now, when we check the output of iwconfig is shows that our external adapter is in monitor mode. Now that we have our adapter configured for this attack, let’s get to it.
Step 2: Sniff for Target Networks
If we’re going to boot ourselves off a wireless network, we’ll need to identify what network we’re on first! For this, we’ll be using a tool called airodump-ng. This will allow us to view all the wireless networks in our area:
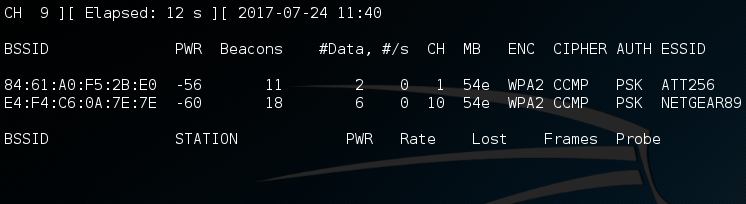
Step 3: Sniff for Victims on the Target Network
Alright, so we have a couple of networks in our vicinity. The network that our built-in adapter is on is NETGEAR89, so let’s do some sniffing specifically for that network. From this information here, we’re going to be using the BSSID and the channel number of the NETGEAR89 network. So, let’s just re-execute airodump-ng and pass it this information:
![]()
Now, once we execute this command, we should be able to see information regarding the clients connected to this wireless access point (WAP):
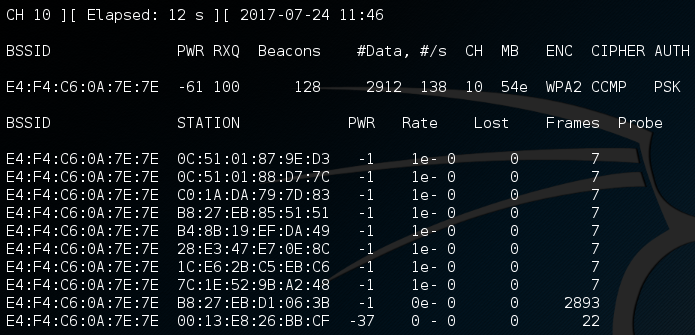
Alright, now that we have this information about the connected clients we can move on to the next part of the attack. (Note: in order for the next part of the attack to work, we need to keep airodump-ng running, so leave this terminal open. I’ve just minimized it to move it out of the way.)
Step 4: Inject Deauthentication Frames into the Target Network
Now that we have the information about the target network, and the clients on said network, we can finally perform our deauthentication attack and boot ourselves off. The tool we’ll be using to inject the deauth frames into the network is aireplay-ng. This is command we’ll use to start aireplay-ng:
![]()
Here we specify the deauth attack and tell aireplay-ng to inject only once. We then use the -a flag to give the BSSID of the target network. Ending the command, we specify the client to deauth by using the -c flag followed by the victim’s MAC address. Now, let’s execute this command and wait.
After the injection is finished, we should be able to take a look at our wireless adapters and see that we are no longer connected to a wireless network:
![]()
There we have it. After our deauth attack, we can see that our PCI (internal) wireless adapter has been disconnected from the wireless network, we did it! This is only the beginning of Wi-Fi hacking here on HackingLoops. In the near future, we’ll be attempting to build our own versions of the tools we used here, so we can develop a better understanding of how these tools works. When we build these tools, we’ll be using Scapy and Python, so if you haven’t read our articles on those topics, I recommend doing so!
The Best Wi-Fi Cracking Tools on Kali Linux
 These
days, there are a lot of different tools that supposedly perform the
same function. This couldn’t be truer of Kali Linux, which is loaded
with different tools that will help people hack Wi-Fi
networks. The only problem for novitiate hackers is awareness. There
are many would-be hackers and security enthusiast that can’t hack Wi-Fi
networks simply because they don’t know what software to use.
These
days, there are a lot of different tools that supposedly perform the
same function. This couldn’t be truer of Kali Linux, which is loaded
with different tools that will help people hack Wi-Fi
networks. The only problem for novitiate hackers is awareness. There
are many would-be hackers and security enthusiast that can’t hack Wi-Fi
networks simply because they don’t know what software to use.
Aircrak-ng
Aircrack-ng is perhaps one of the most widely known and utilized wireless cracking tools for Linux. Using this sophisticated yet intuitive software, even novices can learn how to hack WEP, WPA, and WPA2 security protocols. It’s less of a program and really more of a suite of useful software that helps security professionals capture packets to break the handshaking protocol, bump devices from the wireless network to force them to reconnect (to facilitate and attack), perform dictionary and brute force attacks, and even inject packets into a wireless system. Within this suite of software, there are tools for the following:
- Cracking wireless passwords (aircrack-ng)
- Generating traffic to de-authenticate connected wireless clients (aireplay-ng)
- Capture wireless packets (airodump-ng)
- Create fake access points (airbase-ng)
This software comes standard in the Kali Linux package, assuming that you choose to include the package in the installation process. If not, it can be downloaded and installed for free. The only caveat is that your wireless card needs to have packet injection functionality.
Reaver
Next is Reaver, which is nearly as popular as aircrack-ng. It is a highly sophisticated tool that is aimed at breaking Wi-Fi Protected Setup (WPS). Not only can it perform brute force password attacks, but it can also recover PINs for the WPA/WPA2 security algorithms. Believe it or not, most wireless devices in a home environment have WPS enabled by default, making Reaver incredibly practical.
It’s not perfect, though. Patience is a virtue, and Reaver can typically crack a wireless router in 5 to 10 hours. The length of time depends on a variety of factors including password strength, wireless signal strength, and distance to the access point.
Pixiewps
Though less famous than the preceding two tools, PixieWPS also targets WPS security flaws. Like Reaver, it leverages brute force attacks against WPS PINs to crack wireless networks, aptly named a pixie dust attack. In the scope of security tools, PixieWPS is relatively young, but it has garnered so much popularity that it deserves an honorable mention.
Wifite
Wifite is yet another great tool to crack wireless networks using WEP, WPA, WPA2, and WPS algorithms. However, there are a lot of different parameters to setup before a user can begin using the software. Although, like aircrack-ng, Wifite will do all the heavy lifting for you, making the attack process ludicrously simple. In fact, many would agree that the most tedious part of the process is setting up the software. Not only can it capture the algorithms’ handshakes and de-authenticate connected users, but it can also spoof an attacker’s MAC address.
Wireshark
Wireshark isn’t purely a wireless cracking tool per se. In fact, it is really a full featured packet sniffer that can be used on all of the major operating systems. Using this tool, users can capture data straight from the wire or grab wireless packets out of the air. As such, it is an extremely useful tool for those wishing to analyze and crack wireless networks. Though it is probably too advanced for novices to understand everything they are seeing in Wireshark, it is a handy way to see each and every packet that is being transmitted.
In addition, it has handy filtering features that allow an attacker to sift through different protocol data to analyze a user’s activities. Lastly, it is available on most major operating system platforms, and there is a GUI as well as a Linux command line interface.
oclHashCat
Though it isn’t included in Kali Linux by default, it can capture handshakes and perform a variety of password attacks including dictionary and brute force. One of the real benefits of this tool is that an attacker can use their GPU cycles instead of their CPU to crack a password, thereby offloading the majority of the work and speeding up their local machine. However, it is only available for Linux and Windows, and there are some constraints regarding which GPU’s can be used, such as AMD and Nvidia cards.
Fern Wi-Fi Cracker
Fern was written using Python, and it is an auditing tool in addition to a wireless cracker. While the majority of the preceding applications only have command line interfaces on Linux, Fern actually has a GUI interface. If you’re new to Linux and scared of the command line, Fern might be the best way to ease into cracking tutorials. Like several of the previous tools, it can crack WEP, WPA, and WPS. However, unlike several of the previously mentioned programs, it can even perform a man-in-the-middle attack. It, too, is included in Kali.
Wash
Wash is a little more simple than some of the preceding softwares. Instead of being a full featured cracking and sniffing suite of programs, it is a handy way to see if an access point has enabled WPS before carrying out an attack with another program. Furthermore, users can see if a targeted device, such as a wireless access point, has locked up after too many attempts with Reaver. Yet again, this tool is included with Kali.
Crunch
Though it sounds like a candy bar, Crunch is actually a handy tool that includes features to help attackers and security professionals tailor wordlists than can be stored in a dictionary. You see, no word list will ever be comprehensive. The percentage chance of a successful attack therefore depends upon the quality and size of the word list used. Plus, this tool can integrate with other programs such as aircrack-ng.
Macchanger
Macchanger is a small, simple, and effective tool that does one thing: it helps attackers spoof their MAC address (go figure). This will help attackers mask their true address when carrying out an attack, and it can even spoof a network card to a completely random address.
How to Crack WPA and WPA2 Wi-Fi Encryption Using Kali Linux
 Most people – even nontechnical users – have already heard about Linux operating systems. However, average users aren’t aware of how powerful Kali Linux
is. Kali Linux was designed to be a hacker’s or security professional’s
best friend, since it comes loaded with a variety of tools and programs
that aren’t always available on other operating systems. The real key
advantage is that all of these tools have been prepackaged into one
system, so you’re ready to go when you begin a new installation provided
you install Kali with the right optional packages.
Most people – even nontechnical users – have already heard about Linux operating systems. However, average users aren’t aware of how powerful Kali Linux
is. Kali Linux was designed to be a hacker’s or security professional’s
best friend, since it comes loaded with a variety of tools and programs
that aren’t always available on other operating systems. The real key
advantage is that all of these tools have been prepackaged into one
system, so you’re ready to go when you begin a new installation provided
you install Kali with the right optional packages.
Though Kali Linux can be used for all kinds of security attacks and penetration tests, one of the reasons it has become so infamous is due to its ability to break wireless encryption standards that secure wireless devices such as routers. Once an attacker leverages Kali Linux to break wireless systems, they can provide themselves with full network access. In home settings, the consequences of being hacked may be nominal, but in a professional setting such as an office, an attack could be many times more damaging.
If you are the type of person that is technologically literate and understand the different types of wireless security protocols, you know how easy it is to break certain forms of encryption and security. In this demonstration, we are going to take a step-by-step look at how you can break WPA and WPA2 (Wi-Fi Protected Access 2) using Kali Linux.
What You Will Need for the Demo
First off, you are going to need a Kali Linux installation. If you prefer to install Kali Linux to your hard drive and feel comfortable working with multiple operating systems on a single host computer, feel free to install the software. In addition, you have the option of building your own machine that will run Kali Linux exclusively. However, there is an easier solution.
If you download and install VMWare, you can run a virtual Kali Linux image simultaneously in your host environment, such as Windows. There are a couple of extra configuration steps you will need to make to your virtual machine’s network interface, and there is one additional caveat. By default, there isn’t a way to bridge the internal wireless card in a laptop through to VMWare, so in this case, you would need an external USB wireless adapter. You might find that your wireless hardware isn’t capable of running monitor mode, in which case you can easily purchase a USB wireless card to use in the demonstration.
You will also need a wireless router that you own to practice on. Exercise great caution before applying these techniques, because it would be illegal for you to try to break into a system that you don’t own. Make sure you have the following items together before you begin:
- A computer system with Kali Linux installed
- A wireless router that you own configured to use WPA2
- A wireless card that is capable of running in monitor mode
- The aircrack-ng software
The Attack Process
Once you have all of your hardware together, it’s time to begin the attack process. Note that it would be best to have root privileges on the Kali user account you are using to perform the attack. Otherwise you may have to use the sudo command, which can be extremely tedious.
Step 1
Make sure that your network card is visible in Kali by using the ifconfig command. If you are using a wireless card via USB, ensure that it is plugged in.
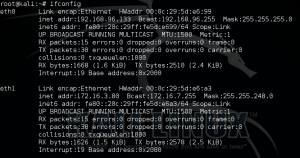
Step 2
Make sure that your computer isn’t currently connected to a wireless network. Then you will need to run the airmon-ng command from the terminal. This command will display all of your wireless interfaces that are capable of running in monitor mode. Unfortunately, if you don’t see any interfaces listed, your card likely isn’t capable of monitor mode.
Step 3
Now you need to actually start using airmon-ng on your wireless interface. In our example, the wireless interface is named wlan0, so we would enter the airmon-ng start wlan0 command. After you have completed this step, output in the lower-right corner of the terminal should display the listening wireless interface (it will likely be named mon0).
Step 4
Next, you will need to run the dump command with the listening wireless interface as a parameter. In our example, the command we would need to enter would be airmon-ng start wlan0. This will show you any information gleaned from wireless networks in range of your wireless card such as the encryption type, the BSSID (essentially the MAC address of the wireless device), and other information such as the channel and model number of the wireless device.
Step 5
Find the wireless network that you want to crack and copy its BSSID. You will need to plug other information from the airodump-ng command into the command that starts the attack procedure. The command we will need to use is as follows:
- airodump-ng -c [wireless channel] –bssid [BSSID] -w /root/Desktop/ [monitor interface]
Remember that the monitoring interface in our example is mon0.
Step 6
The next step can be a little troublesome. By now your wireless interface is gathering and storing information about the wireless network, but in order for the attack to succeed, we will need a host to connect to the wireless network. When a device connects to the wireless router, our Kali software will capture data regarding a four-way handshake that is the weak point in the protocol. If you were performing this in real-life on a live network, there’s no telling how long it could take for a host to connect. Fortunately, since we are doing this in an environment we control, we have the option of connecting another device to the network manually.
Alternatively, you can use a de-authorization command, which feels a lot cooler. Essentially, this command will craft some de-authorization packets to send to the target wireless router to force the reconnection process for other devices. We will target a device to force to reconnect by using the client’s BSSID in a command. The only requirement is that you already need to be able to see a connected client’s BSSID in the previous command’s output.
Step 7
Make sure that you don’t close the terminal that you started running the airodump-ng command. Then, open a second terminal and enter the following command:
- aireplay-ng –0 2 –a [Router-BSSID] –c [Client-BSSID] mon0
Step 8
You should see output that displays the indication of a successful handshake.
If you don’t, however, there are a multitude of factors that could have
caused it to fail. One common problem is that the wireless signal was
too weak, in which case you would only need to move your computer closer
towards the wireless router. In addition, the connected device may not
be configured to automatically reconnect to the network. If that’s the
case, then you will have to wait for them to reconnect (in a real-life
scenario).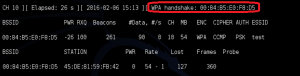
Step 9
Upon a successful reconnection handshake, we are going to need to crack the protocol. Enter the following command, and plug in the parameters as they pertain to your configuration:
- aircrack-ng -a2 -b [Router-BSSID] -w [Wordlist-File] /root/Desktop/*.cap
The only new parameter in this command is a wordlist we have not yet discussed. A wordlist is basically a file containing different character combinations that we will use to carry out the attack. You can find them online for free, just make sure you remember where you store the data on your computer and use the file’s path as a parameter in the preceding command.
After you have entered the command, the software will finally initiate the process of breaking the wireless encryption.
Step 10
Now all you need to do is wait for the software to break the key. Note that in order to successfully break the encryption, the Wi-Fi password needs to be contained in the wordlist. This is called a dictionary-based attack, which is a little different from a brute force attack. A dictionary-based attack simply tries all of the passwords in a list or database whereas a brute force attack tries all possible combinations of characters. If your dictionary failed to find the correct password, you can try using an additional wordlist. Also note that it could take a long time to actually break the password, depending on the strength and complexity of the password as well as how fast your computer hardware is.
Step 11
Once the software successfully cracks the password, it will display the key near the middle of the terminal in a line that reads:
- KEY FOUND! [ wireless key ]
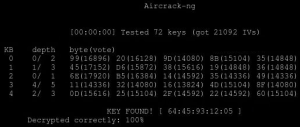
Go ahead and try logging in with the key for fun, though you should already know what the key was since you are using this on your home network.
Final Thoughts
Breaking WPA and WPA2 encryption is pretty easy as far as security attacks are concerned. But please remember to use this information responsibly. You simply don’t have the right to run around war driving and attacking other people’s networks, and the consequences could be terribly severe.
How to Crack WEP Wi-Fi Encryption Using Kali Linux

Today we are going to take a closer look at the vulnerabilities in the WEP (Wired Equivalent Privacy) protocol and see how to exploit those vulnerabilities and how hackers can gain access to a Wi-Fi network they don’t already have access to. We will be using the aircrack-ng software to facilitate the attack from a Kali Linux installation, but I wanted to point out a few caveats, warnings, and explanations before we dig into the demonstration.
First of all, you should note that some of the attack process is similar to cracking the WPA and WPA2 Wi-Fi protocols. However, WEP is a different protocol altogether, so past starting the software on a wireless interface and performing the dumps, the process is a little different. In addition, you should note that we are not going to be taking advantage of a handshaking and reconnection flaw and performing a dictionary-based attack as we did with WPA. Instead, we are going to monitor wireless data and capture packets to deduce the key based on some well-known vulnerabilities.
WEP Vulnerabilities vs WPA Vulnerabilities
Before we begin the WEP cracking demonstration, you should have a general understanding of the protocol, its vulnerabilities, and how they differ from WPA and WPA2. First off, you should understand that WEP is a security protocol that uses RC4 security which is a type of stream cipher. The cipher uses a short key to generate a ‘random’ key stream, but this technology has been exploited for years.
There are several ways that WEP vulnerabilities can be exploited. One way that it is commonly attacked is by comparing two streams that used cipher-texts with identical key streams. By using an XOR operation (Exclusive Or) on the data, the protocol can be reverse engineered.
One of the fatal flaws in the protocol revolve around the CRC-32 checksum that is used to ensure that data hasn’t been changed in transit – otherwise known as an integrity check. By changing the bits and editing the checksum to a valid permutation, it is possible to fool the RC4 stream data into appearing valid. However, this is just the tip of the iceberg regarding WEP vulnerabilities, and you should know that these security flaws give rise to both passive and active attacks.
Conversely, WPA suffers from a security vulnerability related to TKIP (Temporal Key Integrity Protocol). These flaws make WPA and WPA2 vulnerable to packet spoofing, decryption, and brute force attacks. While the underlying mechanics of WEP and WPA are very different, you’ll find that you can crack either protocol in a matter of minutes (usually) by using the aircrack-ng software on Kali.
One of the key differences between our attacks is how we attack the protocol. In the WPA and WPA2 tutorial, we used a dictionary of passwords to find the key. This time, however, we are going to be intercepting wireless packets out of the air with aircrack-ng (though there are many other types of packet sniffers) to discover the key data.
Attack Types
Passive attacks are facilitated by a wiretapping technique that allows an attacker to intercept wireless communications until they spot an ICV collision. Then, the attacker can use software to deduce the contents of the data. Because of the flaws in the RC4 algorithm, an attacker can relatively easily gather data and cross-check that data to decrypt messages and even gain network access.
Conversely, and active attack can be used when an attacker already knows the plaintext data for an encrypted message. Then, the attacker can manually craft additional encrypted packets to fool the WEP device. Because they know how to manipulate the hashing algorithm, they can fool the integrity checks, causing the WEP device to erroneously accept the packets as valid data. This is a type of injection attack, and they are surprisingly easy to carry out.
Getting Started
Before you begin, you are going to need several things to build an environment where you can begin hacking. As always, you should know that you don’t have the legal right to misuse this information in public to attack real-life networks, so you should only attempt this exploit in the privacy of your home network. You are going to need the following five items before we can begin:
- A computer system running Kali Linux
- A wireless router using WEP that you own and control
- The aircrack-ng software
- A wireless interface that can be run in monitor mode to collect packets
- Another wireless host connected to the router
Step 1
Make sure your wireless card is seen in your Kali Linux system. You can run the ifconfig command to look for wireless interfaces. You should see an Ethernet and loopback interface, but we are interested in the interface that starts with a ‘w.’ Likely, the wireless interface you want to use will be wlan0 unless you have multiple wireless cards.
Step 2
Next, we are going to use aircrack-ng to put your wireless interface into monitor mode, which will allow it to monitor and capture wireless frames from other devices to facilitate the attack. You will need to run the following command:
- aircrack-ng start wlan0
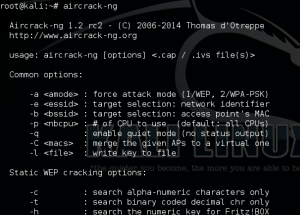 Note that you may have a wireless interface with a different name. If your interface’s name is wlan1
or it has a different name, append it to the end of the command. Make
special note of the output, because it will create a listening
interface, likely named mon0.
Note that you may have a wireless interface with a different name. If your interface’s name is wlan1
or it has a different name, append it to the end of the command. Make
special note of the output, because it will create a listening
interface, likely named mon0.
Step 3
Then we will start using the dump command to grab packets from other wireless devices, and the software will be able to make calculations and comparisons among the data to break the insecure WEP protocol. Enter the following command:
- airodump-ng mon0
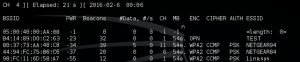
Step 4
Now it is time to tell your wireless interface to start storing captured wireless data based on the network of your choosing. Remember to plug in three key pieces of information from the previous output into the following command:
- airodump-ng –w [ESSID] –c [Channel] –bssid [BSSID] mon0
More specifically, you will need to plug in the ESSID, the channel number (CH), and the BSSID. By now your wireless interface should be capturing wireless frames, but you are going to need to store them in a local file. You will want to have at least 10,000 packets before you move on to the remaining steps. Use the following command to write your data to a file on your hard drive:
- airodump-ng mon0 –[file-name]
Step 5
Last but not least, you are going to need to do the most important step of the process by actually using the captured data from the WEP device. Issue the following command:
- aircrack-ng [file-name].cap
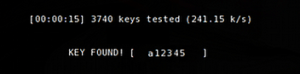
If all goes according to plan, you should be able to break the WEP system. However, if the command fails, you will want to wait until your wireless card captures more data. Give it time to capture 15,000 packets and then try again.
Caveats and Differences from WPA
You’ll probably note that the attack procedure has fewer steps than the WPA/WPA2 attack procedure. While it may seem simpler on the surface, you should know that the WEP attack process revolves around capturing data transmitted by other wireless hosts. If there is only one host connected to the network or hosts aren’t sending much data, it will take longer to gather enough data for the attack to work. On the other hand, the WPA/WPA2 attack centered around using a dictionary of passwords after forcing a host to reconnect.
Final Thoughts
It is a simple matter to break WEP encryption provided you have the right tools, but be warned. You shouldn’t ever abuse this knowledge. Doing so could lead to severe consequences that negatively impact your life. Make sure that you only attempt these attacks on devices that you own, and make sure that you never use WEP to secure your wireless access points and routers.
Comments