How to Generate Custom Wordlists for Password Cracking
How to Generate Custom Wordlists for Password Cracking
Password cracking is one of the dominant practices used in Cybersecurity. Security professionals use the technique for auditing purposes whereas hackers use password cracking to gain unauthorized access to networks, systems, applications, etc. In 2019 Verizon’s Data Breach Investigations Report (DBIR), 29% of the total breaches were reported as a result of stolen credentials. This large percentage of successful passwords security breach shows the popularity of this threat action among hackers’ community. Dictionary, Bruteforce, Hybrid, and Rainbow Table are the common approaches used in offline and online password cracking techniques. The online method depends on the network speed while the offline password cracking methodology heavily depends on the computing machine. The dictionary approach is used for attempting common passwords whereas the brute-force approach is applied for more complex passwords. Different wordlists are available to aid the dictionary and brute-force attacks. The majority of these wordlists contain random passwords or credentials from the leaked passwords databases of different organizations. Although these wordlists have a great capacity to crack common passwords, they are less effective in cases where there is a likelihood of use of personal information in secret credentials. The use of personal information like name, age, contact number; date of birth, home town, etc. in secret credentials is human nature. Such information should be incorporated into the wordlists to make the password cracking process more effective against targets with known attributes. Following is a brief overview of the wordlists analysis method followed by a custom wordlist generation technique.
Analyzing Wordlists Using Pipal Tool
Pipal is a passwords analysis tool that gives a number of useful stats about passwords under review. Security analysts can use the tool for auditing the cracked passwords whereas the penetration testers can analyze the wordlists before using them for password cracking attacks.
Pipal Installation
Pipal is a Ruby-based tool that requires a source package to operate. The source files can be downloaded using the following command.
git clone https://github.com/digininja/pipal.git
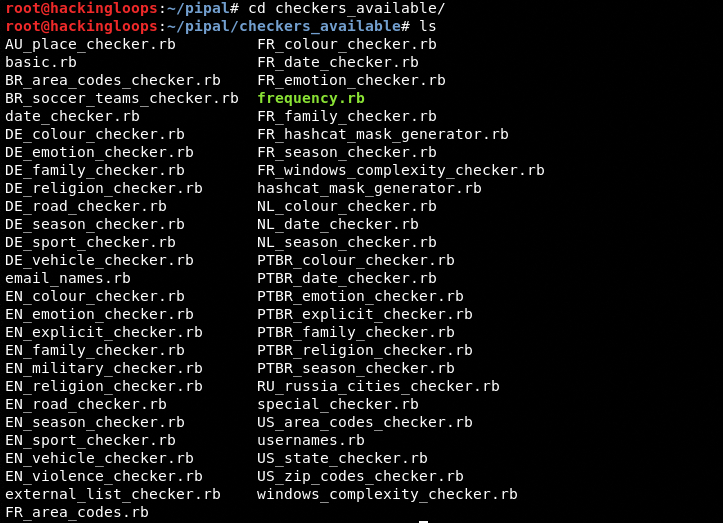
The tool uses a basic checker as a default module to analyze the passwords. There are advanced checker modules available in checkers_available directory as shown in the following screenshot.
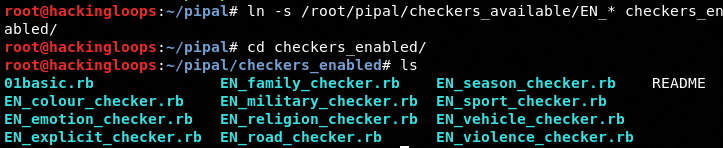
The available modules can be cloned to checkers_enabled modules directory using the following command.
ln –s <checkers_available directory path/selected modules> <checkers_enabled path/directory>
We have enabled all the modules with EN prefix.
ln –s root/pipal/checkers_available/EN_* checkers_enabled/
The linking of the newly enabled modules can be confirmed by visiting the checkers_enabled directory.
How to Analyze Wordlists
Analyzing wordlists using Pipal is a straight forward process. Define the number of top results (stats), wordlist file path, and optional result file and path in the following format.
./pipal.rb --top <number of top results to show> <target wordlist path and file name> -o <optional output file path and name>
For demonstration purposes, we have analyzed 0.2 million passwords from the default rockyou.txt wordlist found in Kali Linux with the top 100 results.
./pipal.rb –top 100 <target wordlist path and file name> -o password-analysis.txt
We have found that the majority of passwords in the Kali Linux rockyou.txt file were only six digits.
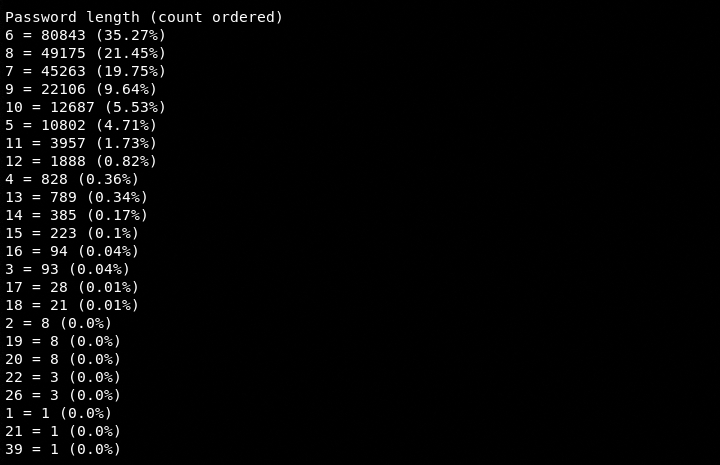
Top 100 base passwords were common lower case words.
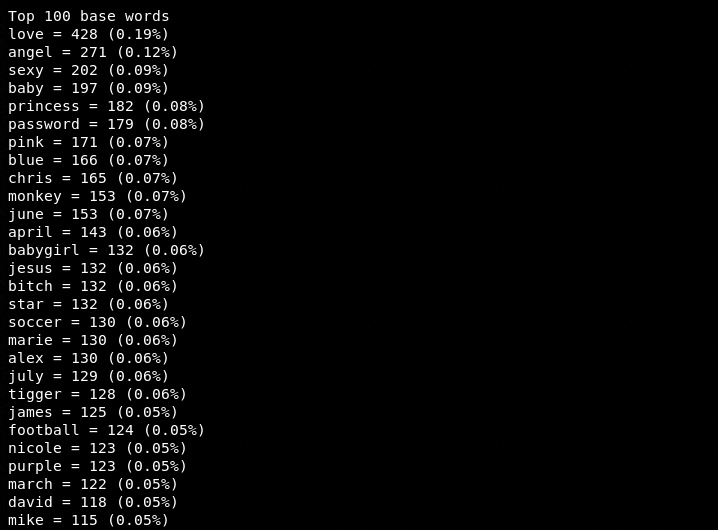
The characters’ frequency of the analyzed passwords can be seen in the following screenshot.
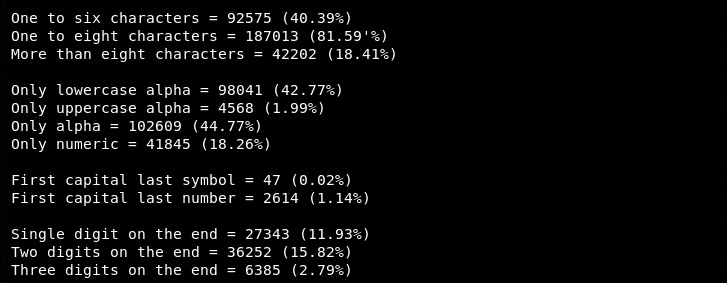
The aforementioned results from the default wordlist clearly suggest that the wordlist is less effective against the modern-day complex passwords. Hence, we need custom wordlists containing alphanumeric and special characters to Bruteforce the more complex passwords with greater success.
Generating Custom Wordlists Using BEWGor and Mentalist Tools
The Mentalist is a GUI-based tool that can create wordlists according to the seed passwords. Seed passwords are the base passwords provided as an input to the Mentalist tool. BEWGor tool has the ability to generate custom seed passwords that can be used as base passwords to generate a rich wordlist file for dedicated password cracking tasks.
BEWGor Installation
Clone BEWGor tool from Github using the following command.
git clone https://github.com/berzerk0/BEWGor.git
Generating Base Passwords Using BEWGor Tool
Navigate to the BEWGor tools directory and run the BEWGor.py file with –input parameter as shown in the following command.
python BEWGor.py –input
The tool asks some basic questions about the target to create a custom wordlist that should contain password entries based on target profiling.
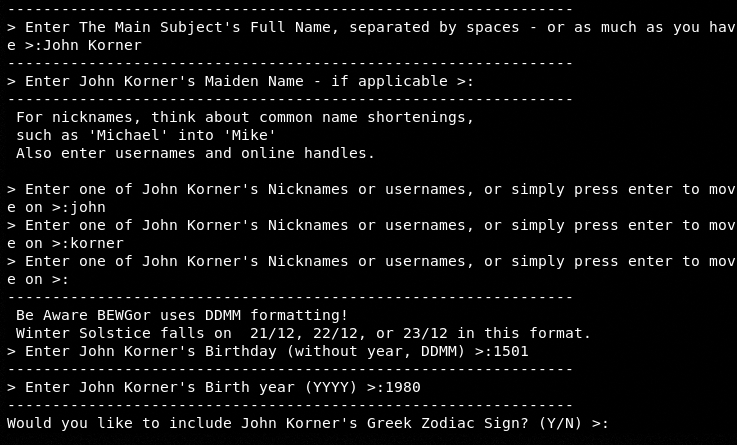
Although BEWGor can be used as a standalone wordlists generator, we are using the tool to generate custom base passwords for Mentalist.
Generating Comprehensive Custom Wordlist Using Mentalist Tool
The Mentalist is a GUI-based tool that can effectively generate wordlist with millions of entries based on the seed passwords and custom user input parameters.
Mentalist Installation
Clone the Mentalist tool from Github using the following command.
git clone https://github.com/sc0tfree/mentalist.git
Navigate to the tool’s directory and run the following commands to complete the installation process.
cd mentalist python3 setup.py install
How to Generate Wordlist Using Mentalist Tool
Typing the mentalist keyword in the command-line interface opens the graphical user interface of the tool as shown below.
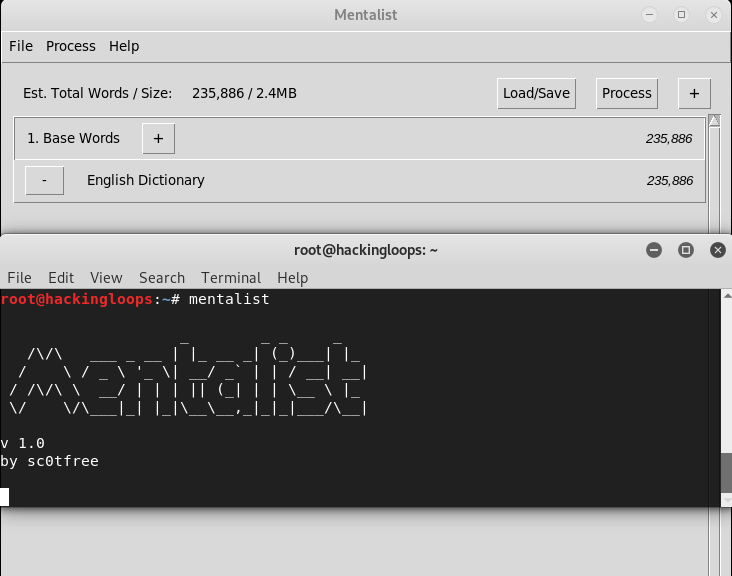
The plus (+)sign in the top right corner of the tool adds the case, substitution, append and prepend features to the wordlist.
Click on the plus symbol (+) next to the base passwords text to select the base passwords file generated by the BEWGor tool.
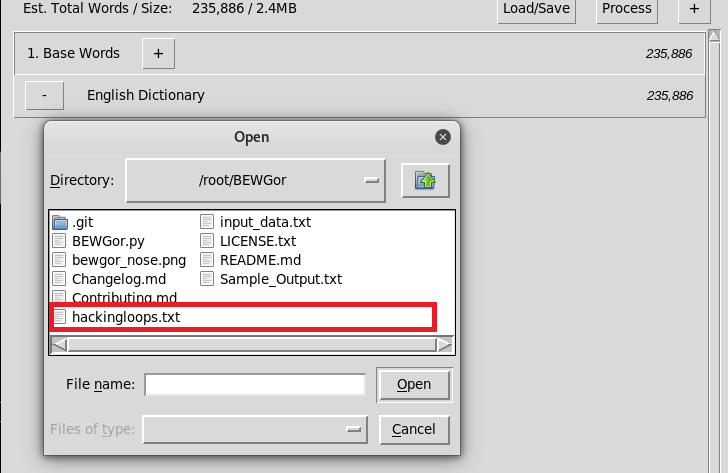
Select the case, substitution, append, and prepend option parameters to customize the wordlist according to the requirement of the password cracking attack. We have selected the following parameters.
1) Selected Case Parameters

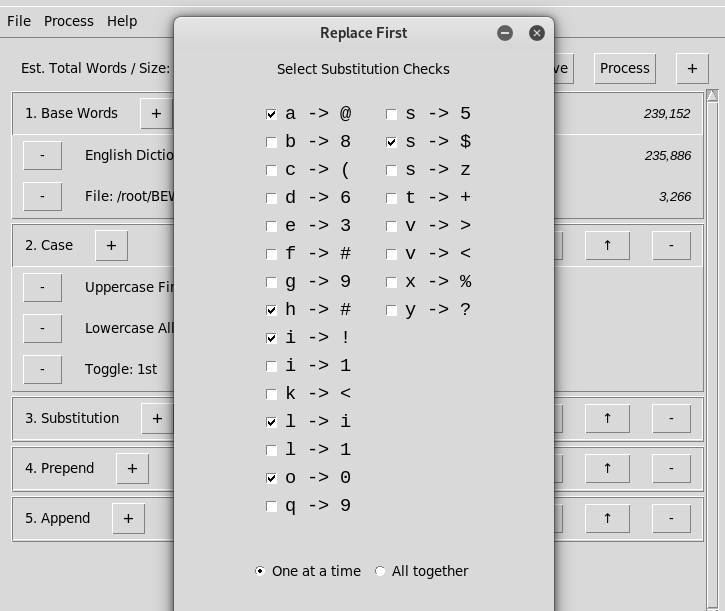
2) Selected Substitution Parameters
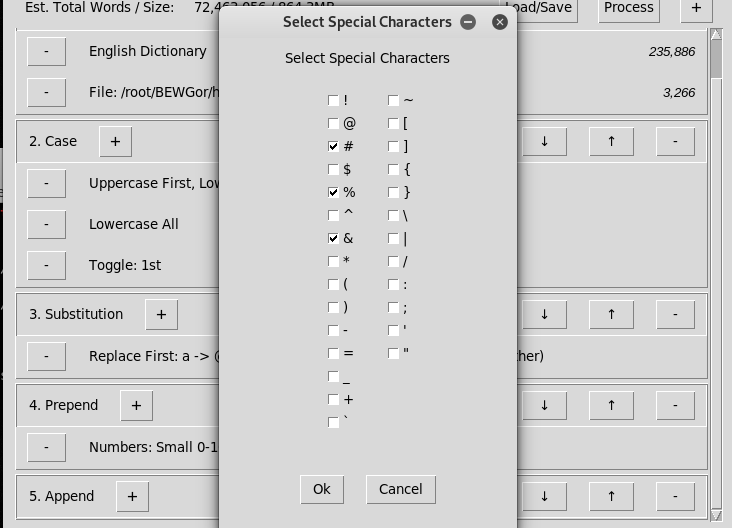
3) Selected Append Parameters
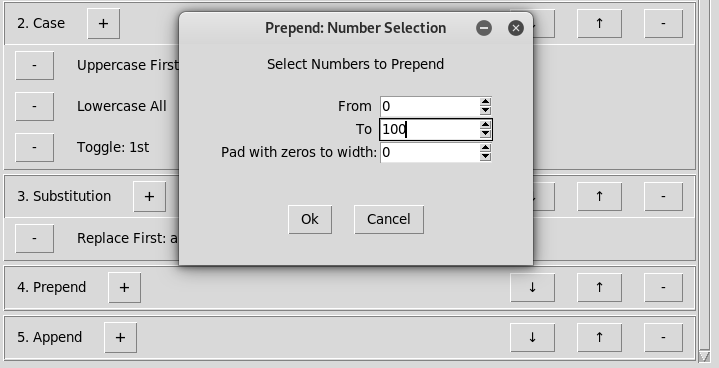
4) Selected Prepend Parameters
The following screenshot shows the summary of the selected parameters and possible wordlist length. The current configurations can generate a wordlist with more than 200 million entries.
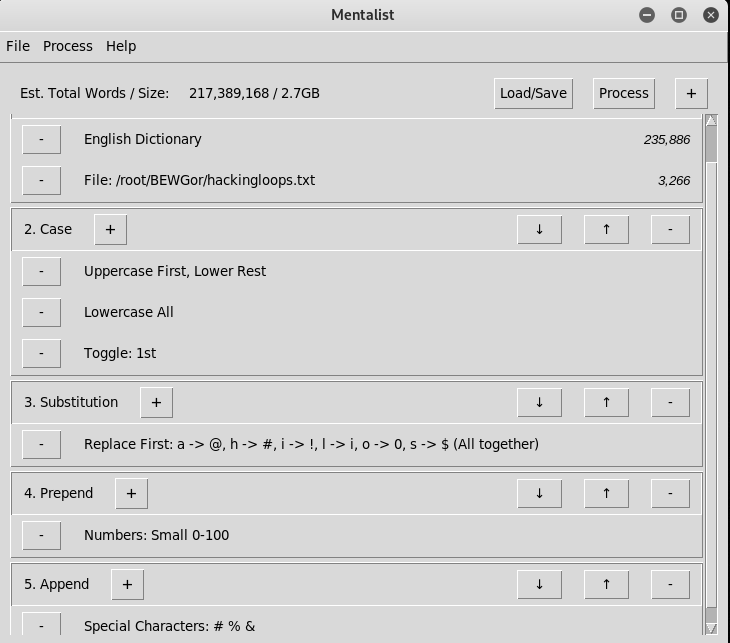
Save the wordlist with the desired name and file path.
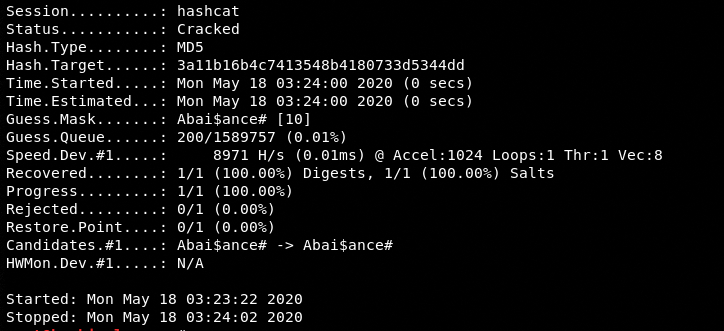
Testing Custom Wordlist with Hashcat Tool
We have tested the newly created wordlist against a complex password using the Hashcat tool. The results show that our custom wordlist is capable of cracking the complex password hashes compared to the default rockyou.txt file.
Conclusion
The 2019 Verizon’s DBIR suggests that organizations (and individuals) should implement strong secret credentials policy in order to reduce the security breaches due to stolen passwords. A regular credentials security audit should be organized to lower the frequency of password attacks. Custom wordlists should be used in combination with the default and leaked passwords lists to achieve the desired password cracking results.




Comments