Which Discovery Technique is Best: OSINT OR Bruteforce?
Which Discovery Technique is Best: OSINT OR Bruteforce?
Subdomains are used to test, develop, or often host applications and services that are skipped from the official domains. In Cybersecurity, subdomains are important for two main reasons; they increase the attack surface; there is a great possibility of security bugs in subdomains as compared to the main domain of a business or platform. Therefore, analyzing subdomains is an important phase of penetration testing. OSINT and Bruteforce (also known as Wordlist) methods are two widely used methods of finding subdomains. Many subdomain discovery tools are built on these two techniques. In the following section, we analyze both techniques while learning the working of different subdomain discovery tools used in penetration testing.
A) BRUTEFORCE Technique
In bruteforce technique, different wordlists are used to bruteforce each name on the list. The scanning process highly depends on the wordlists used by the tools. Although it is a slow technique, the results of Bruteforce method are mostly accurate. We have selected DNScan and Knock tools to analyze the working of Bruteforce technique
1) DNSCAN Tool
DNScan is a wordlists based subdomain scanner that runs each entry in the provided list and verifies the discovered subdomains. DNScan comes with a number of default wordlists. According to its developer, the wordlists in the tool are created by analyzing the most common and popular subdomains names from the web. We can also add manual entries or provide a custom wordlist to check the subdomains for desired host.
How to Install DNScan?
DNScan is a Python script that can be cloned using the following command.
git clone https://github.com/rbsec/dnscan.git subdomains/dnscan
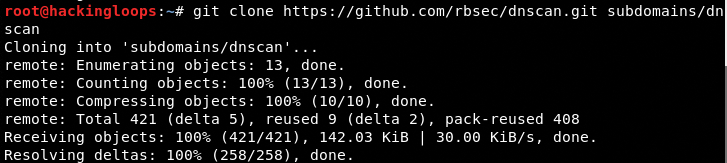
[Note: the subdomains/dnscan is the optional directory we are using to store the package]
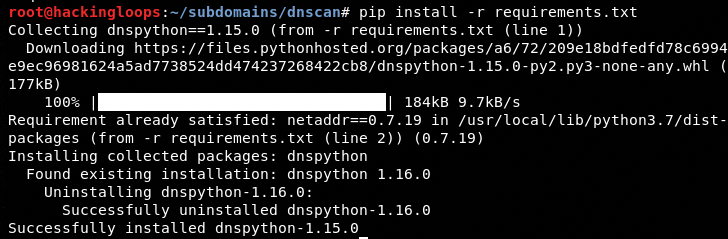
The dependencies can be installed by navigating to the package directory and executing the requirments.txt file using the following command.
cd subdomains/dnscan pip install –r requirements.txt
How DNScan Works?
The DNScan help command shows all the required and optional parameters that can be used in combination to initiate the scanning process.
python dnscan.py –h
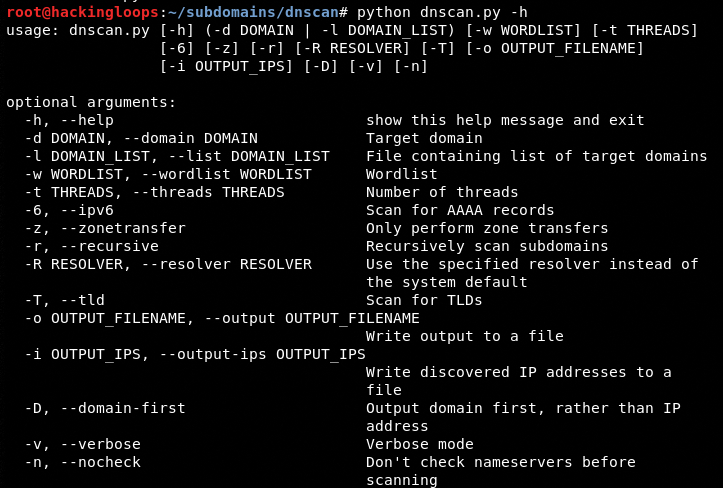
Following is a default method of scanning subdomains using the DNScan tool.
dnscan.py -d <target domain> -l <selected wordlist>
The following screenshot shows the precompiled wordlists available in the tool.
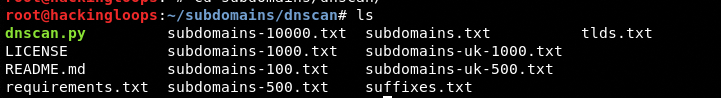
For demonstration purposes, we are using the subdomains.txt file against a test domain <webscantest.com>.
python dnscan.py –d webscantest.com –l subdomains.txt
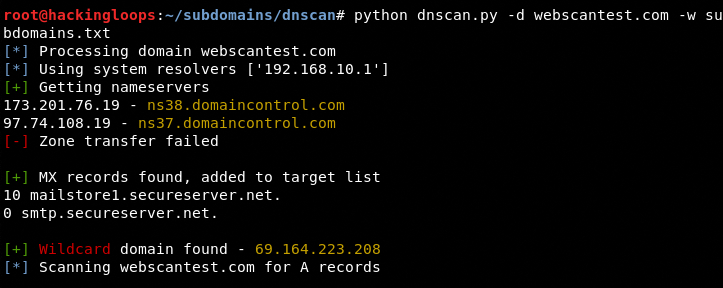
DNScan failed to fetch subdomains for the target host since no entry in the wordlist matched with the potential subdomain names of the target host. We can safely assume that the target host is using non-popular or uncommon subdomain names with reference to the current wordlist (subdomains.txt). By repeating the scanning process for another domain, the tool successfully fetched the subdomains as shown in the following screenshot.
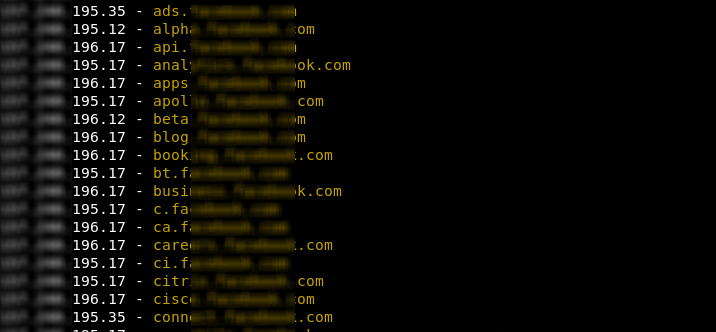
2) Knockpy Tool
Knockpy is another popular wordlist based subdomain discovery tool that utilizes the bruteforce technique.
How to Install Knockpy Tool?
In order to install the Knockpy tool, clone the source code files from Github using the following command.
git clone https://github.com/SolomonSklash/knock.git subdomains/knock
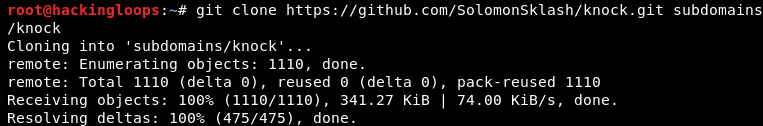
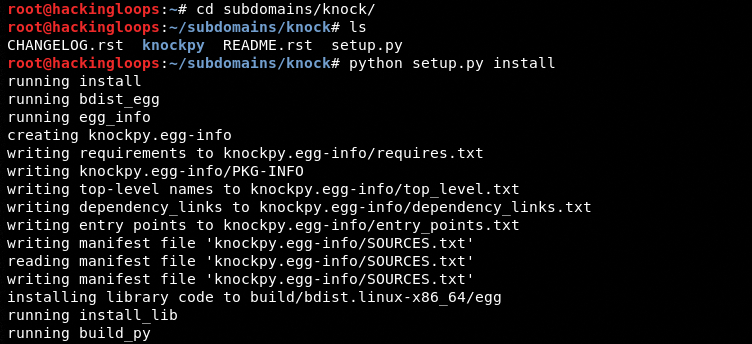
Navigate to the tool’s directory and run the setup file using the following commands.
python setup.py install
How Knockpy Tool Works?
The Knockpy tool has a default wordlist file that is used to bruteforce the entries for potential subdomain names. The scanning process can be initiated using the following command.
knockpy webscantest.com
The tool verifies the server information of the target host before starting the subdomain discovery process.
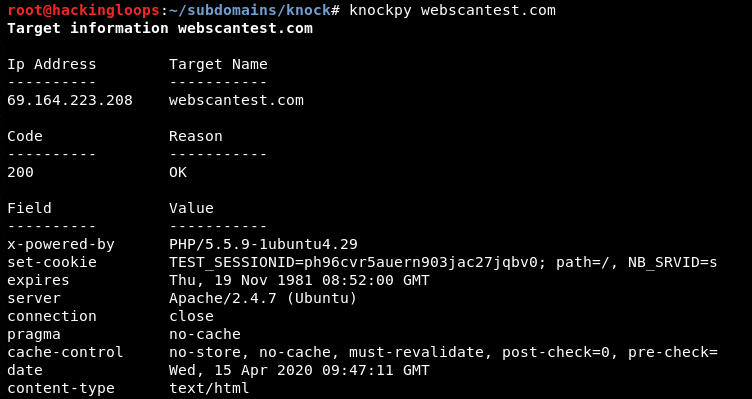
After verifying the host, the default wordlist is loaded to initiate the scanning process.
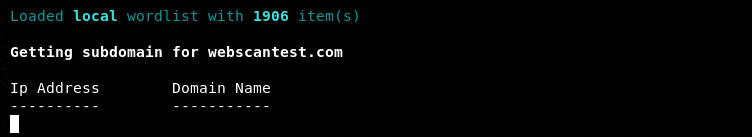
Again, we have noticed that the tool takes a lot of time to test and verify the potential subdomain entries. The success ratio of the tool is found low against unpopular domains as compared to the most common domains.
B) OSINT Technique
The Open Source Intelligence (OSINT) technique is a popular method of finding subdomains. Although the scanning process is fast in OSINT technique, the accuracy can be an issue in some cases. We have selected the Subfinder and Sublist3r tool to demonstrate the OSINT technique of finding subdomains.
1) Subfinder
The Subfinder tool uses a passive method of finding subdomains by querying the online sources. Currently, there are 26 online sources used by the tool for subdomains discovery tasks.
How to Install Subfinder?
The Subfinder is a Go1.13+ dependent tool that is supported by Darwin, Linux, and Windows OS. Different OS installation packages can be found in the form of pre-built binaries on the following release page.
https://github.com/projectdiscovery/subfinder
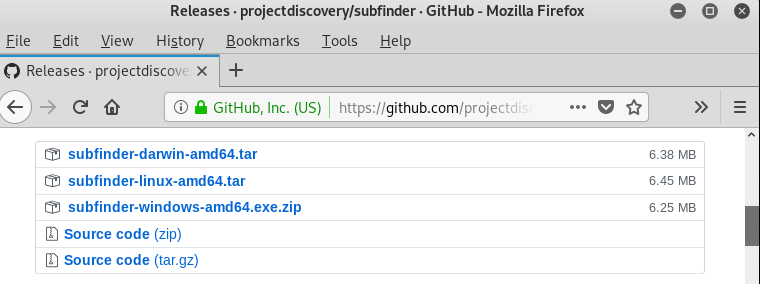
Download and extract the binaries using the following command.
tar -xzvf subfinder-linux-amd64.tar
[Note: The subfinder-linux-amd64.tar in the above command is the name of the downloaded package based on our current OS. The name should be replaced accordingly.]
The next step is to move the Subfinder binaries file to the $PATH. This can be done either by manually copying the file to the /USR/BIN directory in Linux OS or using the following command.
mv subfinder-linux-amd64 /usr/bin/subfinder
How Subfinder Works?
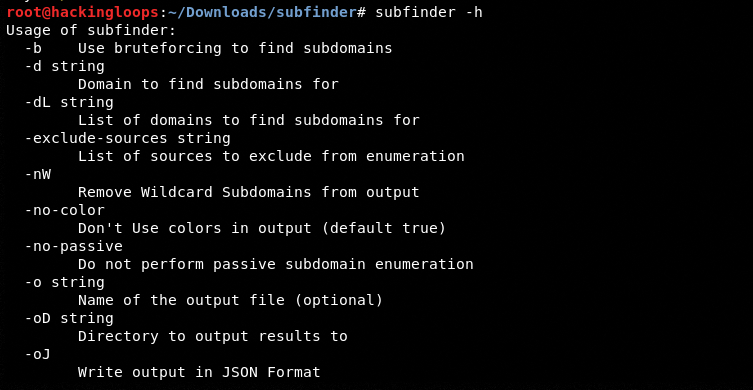
The Subfinder usage options can be explored using the help command.
subfinder –h
We can use the following command format to scan the target for subdomains.
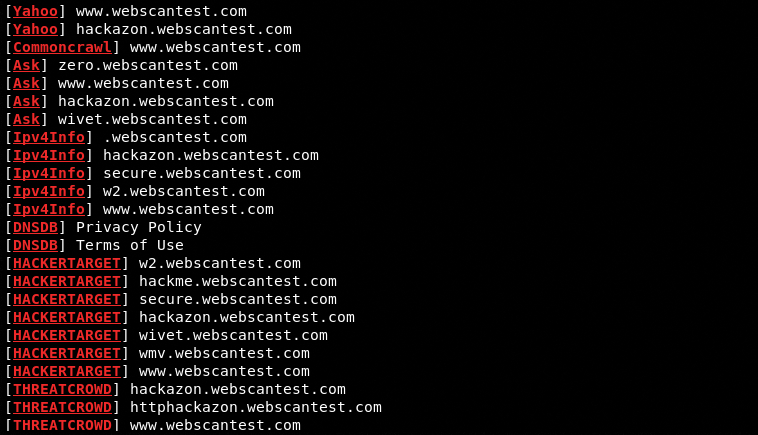
subfinder –d <target domain> -v <optional verbose mode>
The tool uses a number of passive online sources to find out the available subdomains. The results are displayed according to the online sources and discovered subdomains.
2) Sublist3r Tool
Sublist3r is another popular penetration testing tool that utilizes OSINT technique for finding subdomains. The tool uses different search engines as well as online sources like Threatcroud, Netcraft,DNSdumpster, and Virustotal to find the subdomains.
How to Install Sublist3r?
The source code for the Sublist3r tool can be downloaded using the following command.
git clone https://github.com/aboul3la/Sublist3r.git
The Sublist3r requirements can be installed by running the requirements.txt file.
pip install –r requirements.txt
How Sublist3r Works?
Use the following help command to see all the basic options and switches.
python sublist3r.py –h
The scanning process can be initiated by running the following command.
python sublist3r.py –d <target host>
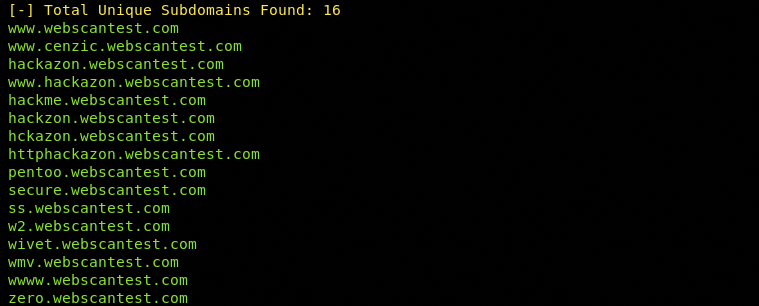
The summary of the scan results is displayed on the screen as shown in the following screenshot.
Conclusion
The performance of subdomain discovery tools is highly dependent on the discovery technique. Each technique has its pros and cons. The wordlist technique is less effective in the case of domains that don’t use common or popular subdomain extensions. However, the results of the wordlist (bruteforce) technique are accurate. The performance of OSINT dependent tools is low against the subdomains that are restricted from appearing in search engines and other online resources. However, the method is fast as compared to bruteforce technique. Therefore, it is wise to use a combination of tools to test target domains using every possible technique to gain maximum results.




Comments